This is archived documentation for InfluxData product versions that are no longer maintained. For newer documentation, see the latest InfluxData documentation.
The Chronograf Admin provides InfluxDB user management for InfluxDB OSS and InfluxDB Enterprise users.
Note: For details on Chronograf user authentication and management, see Managing security.
On this page:
Enabling authentication
Follow the steps below to enable authentication. The steps are the same for InfluxDB OSS instances and InfluxEnterprise clusters.
InfluxEnterprise clusters: Repeat the first three steps for each data node in a cluster.
Step 1: Enable authentication.
Enable authentication in the InfluxDB configuration file.
For most Linux installations, the configuration file is located in /etc/influxdb/influxdb.conf.
In the [http] section of the InfluxDB configuration file (influxdb.conf), uncomment the auth-enabled option and set it to true, as shown here:
[http]
# Determines whether HTTP endpoint is enabled.
# enabled = true
# The bind address used by the HTTP service.
# bind-address = ":8086"
# Determines whether HTTP authentication is enabled.
auth-enabled = true #
Step 2: Restart the InfluxDB service.
Restart the InfluxDB service for your configuration changes to take effect:
~# sudo systemctl restart influxdb
Step 3: Create an admin user.
Because authentication is enabled, you need to create an admin user before you can do anything else in the database.
Run the curl command below to create an admin user, replacing:
localhostwith the IP or hostname of your InfluxDB OSS instance or one of your InfluxEnterprise data nodeschronothanwith your own usernamesupersecretwith your own password (note that the password requires single quotes)~# curl -XPOST "http://localhost:8086/query" --data-urlencode "q=CREATE USER chronothan WITH PASSWORD 'supersecret' WITH ALL PRIVILEGES"
A successful CREATE USER query returns a blank result:
{"results":[{"statement_id":0}]} <--- Success!
Step 4: Edit the InfluxDB source in Chronograf.
If you’ve already connected your database to Chronograf, update the connection configuration in Chronograf with your new username and password. Edit existing InfluxDB database sources by navigating to the Chronograf configuration page and clicking on the name of the source.
InfluxDB OSS User Management
On the Chronograf Admin page:
- View, create, and delete admin and non-admin users
- Change user passwords
- Assign admin and remove admin permissions to or from a user
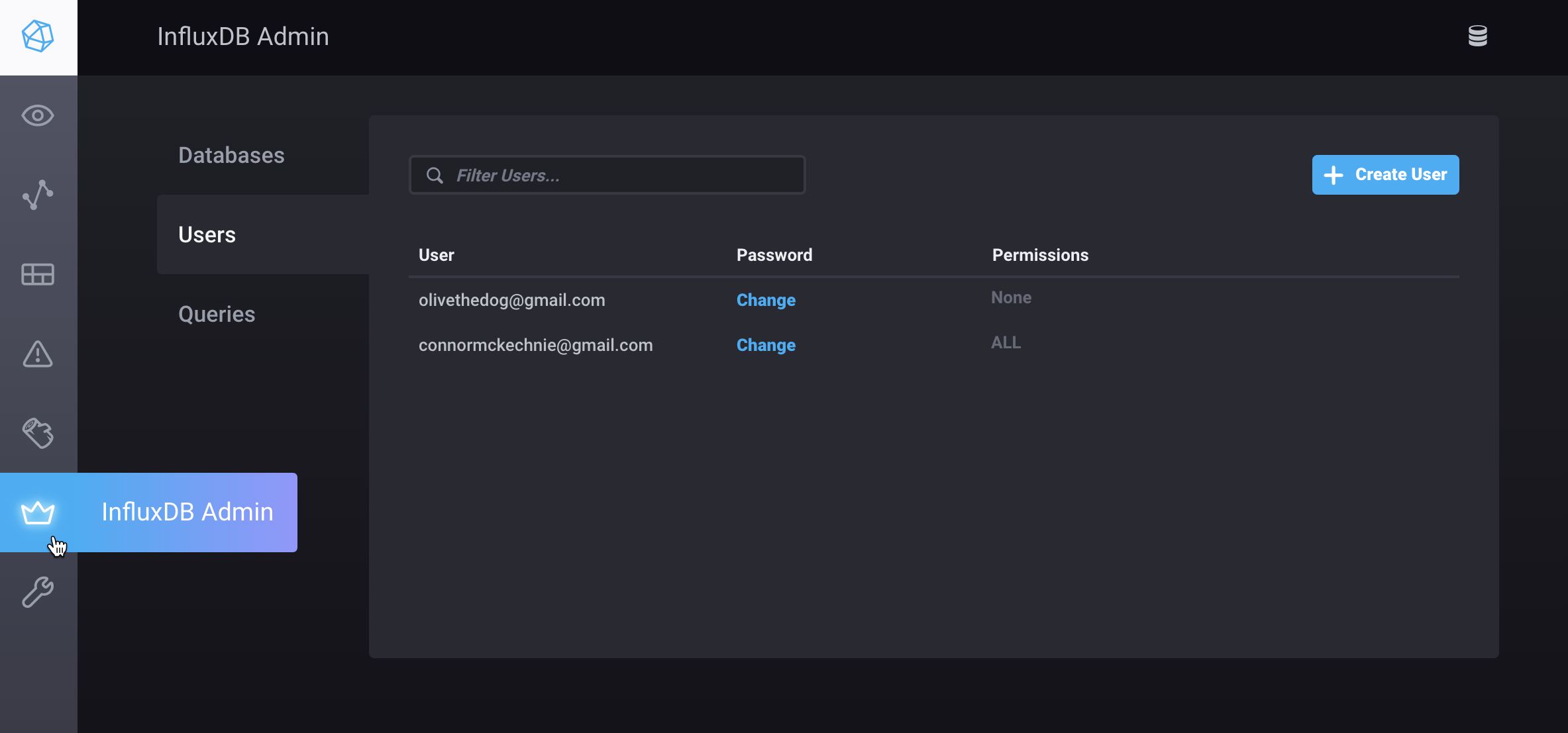
InfluxDB users are either admin users or non-admin users. See InfluxDB’s authentication and authorization documentation for more information about those user types.
Note: Note that Chronograf currently does not support assigning InfluxDB database
READorWRITEaccess to non-admin users. This is a known issue.As a workaround, grant
READ,WRITE, orALL(READandWRITE) permissions to non-admin users with the following curl commands, replacing anything inside< >with your own values:
Grant READ permission:
~# curl -XPOST "http://<InfluxDB-IP>:8086/query?u=<username>&p=<password>" --data-urlencode "q=GRANT READ ON <database-name> TO <non-admin-username>"
Grant WRITE permission:
~# curl -XPOST "http://<InfluxDB-IP>:8086/query?u=<username>&p=<password>" --data-urlencode "q=GRANT WRITE ON <database-name> TO <non-admin-username>"
Grant ALL permission:
~# curl -XPOST "http://<InfluxDB-IP>:8086/query?u=<username>&p=<password>" --data-urlencode "q=GRANT ALL ON <database-name> TO <non-admin-username>"
In all cases, a successful GRANT query returns a blank result:
{"results":[{"statement_id":0}]} <--- Success!
Remove READ, WRITE, or ALL permissions from non-admin users by replacing GRANT with REVOKE in the curl commands above.
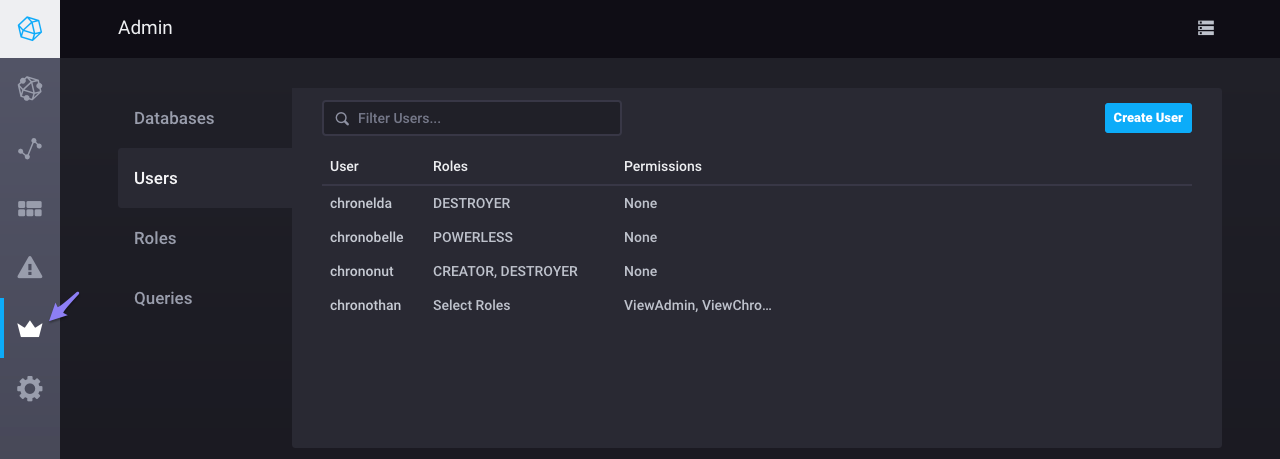
InfluxDB Enterprise user management
On the Admin page:
- View, create, and delete users
- Change user passwords
- Assign and remove permissions to or from a user
- Create, edit, and delete roles
- Assign and remove roles to or from a user
User types
Admin users have the following permissions by default:
- CreateDatabase
- CreateUserAndRole
- DropData
- DropDatabase
- ManageContinuousQuery
- ManageQuery
- ManageShard
- ManageSubscription
- Monitor
- ReadData
- WriteData
Non-admin users have no permissions by default. Assign permissions and roles to both admin and non-admin users.
Permissions
AddRemoveNode
Permission to add or remove nodes from a cluster.
Relevant influxd-ctl arguments:
add-data,
add-meta,
join,
remove-data,
remove-meta, and
leave
Pages in Chronograf that require this permission: NA
CopyShard
Permission to copy shards.
Relevant influxd-ctl arguments:
copy-shard
Pages in Chronograf that require this permission: NA
CreateDatabase
Permission to create databases, create retention policies, alter retention policies, and view retention policies.
Relevant InfluxQL queries:
CREATE DATABASE,
CREATE RETENTION POLICY,
ALTER RETENTION POLICY, and
SHOW RETENTION POLICIES
Pages in Chronograf that require this permission: Dashboards, Data Explorer, and Databases on the Admin page
CreateUserAndRole
Permission to manage users and roles; create users, drop users, grant admin status to users, grant permissions to users, revoke admin status from users, revoke permissions from users, change user passwords, view user permissions, and view users and their admin status.
Relevant InfluxQL queries:
CREATE USER,
DROP USER,
GRANT ALL PRIVILEGES,
GRANT [READ,WRITE,ALL],
REVOKE ALL PRIVILEGES,
REVOKE [READ,WRITE,ALL],
SET PASSWORD,
SHOW GRANTS, and
SHOW USERS
Pages in Chronograf that require this permission: Data Explorer, Dashboards, Users and Roles on the Admin page
DropData
Permission to drop data, in particular series and measurements.
Relevant InfluxQL queries:
DROP SERIES,
DELETE, and
DROP MEASUREMENT
Pages in Chronograf that require this permission: NA
DropDatabase
Permission to drop databases and retention policies.
Relevant InfluxQL queries:
DROP DATABASE and
DROP RETENTION POLICY
Pages in Chronograf that require this permission: Data Explorer, Dashboards, Databases on the Admin page
KapacitorAPI
Permission to access the API for InfluxKapacitor Enterprise. This does not include configuration-related API calls.
Pages in Chronograf that require this permission: NA
KapacitorConfigAPI
Permission to access the configuration-related API calls for InfluxKapacitor Enterprise.
Pages in Chronograf that require this permission: NA
ManageContinuousQuery
Permission to create, drop, and view continuous queries.
Relevant InfluxQL queries:
CreateContinuousQueryStatement,
[DropContinuousQueryStatement](), and
ShowContinuousQueriesStatement
Pages in Chronograf that require this permission: Data Explorer, Dashboards
ManageQuery
Permission to view and kill queries.
Relevant InfluxQL queries:
SHOW QUERIES and
KILL QUERY
Pages in Chronograf that require this permission: Queries on the Admin page
ManageShard
Permission to copy, delete, and view shards.
Relevant InfluxQL queries:
DropShardStatement,
ShowShardGroupsStatement, and
ShowShardsStatement
Pages in Chronograf that require this permission: NA
ManageSubscription
Permission to create, drop, and view subscriptions.
Relevant InfluxQL queries:
CREATE SUBSCRIPTION,
DROP SUBSCRIPTION, and
SHOW SUBSCRIPTIONS
Pages in Chronograf that require this permission: Alerting
Monitor
Permission to view cluster statistics and diagnostics.
Relevant InfluxQL queries:
SHOW DIAGNOSTICS and
SHOW STATS
Pages in Chronograf that require this permission: Data Explorer, Dashboards
ReadData
Permission to read data.
Relevant InfluxQL queries:
SHOW FIELD KEYS,
SHOW MEASUREMENTS,
SHOW SERIES,
SHOW TAG KEYS,
SHOW TAG VALUES, and
SHOW RETENTION POLICIES
Pages in Chronograf that require this permission: Admin, Alerting, Dashboards, Data Explorer, Host List
WriteData
Permission to write data.
Relevant InfluxQL queries: NA
Pages in Chronograf that require this permission: NA
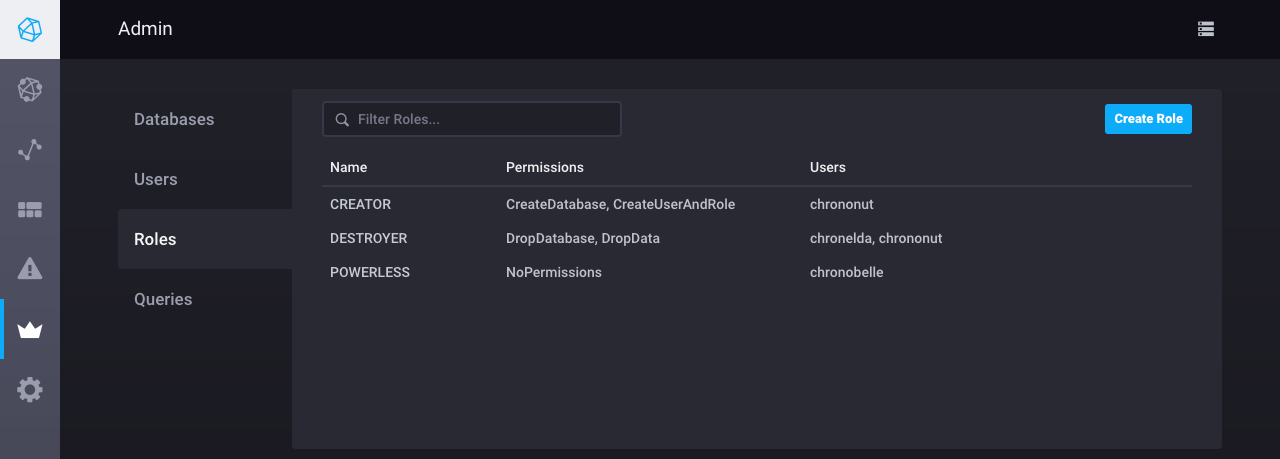
Roles
Roles are groups of permissions. Assign roles to one or more users.
For example, the image below contains three roles: CREATOR, DESTROYER, and POWERLESS.
CREATOR includes two permissions (CreateDatbase and CreateUserAndRole) and is assigned to one user (chrononut).
DESTROYER also includes two permissions (DropDatabase and DropData) and is assigned to two users (chrononut and chronelda).